|
|
|
|
|
RESOURCES’ IDENTIFICATION IN EDUCATION SYSTEMS
1 Department
of Physical Sciences Education, Faculty of Education, Modibbo Adama University, Yola, Adamawa, Nigeria
|
|
ABSTRACT |
||
|
The use of
computers and internet for sharing information has proved to be reliable and
cost-effective. Therefore, use of ICT in education systems is likely continue increasing in contributing to the efficiency of
educational record keeping. However, it is necessary to secure computer
equipment and information systems. Consequently, proactive measures to ensure
security of data in education system is extremely important. This means
education systems administrators, education policy
makers and stakeholders need to have standard safety measures. The core
governing principle for good standing information security posture in modern
organization is confidentiality, integrity and availability (CIA). First,
confidentiality is make data available or disclosed
to authorize users only. Second, integrity is to
preserve the accuracy and completeness of data both at rest and on-transit.
Third, availability is to make information in education systems timely and
reliably accessible to authenticated and authorized users. These security
goals relies on adequate identification system.
Identification is the key that verifies the authenticity of users and evaluate if a user is authorize
to access the system. This paper provide
identification technologies for both human and material resources in
education systems. Since education data are stored in database,
identification is a fundamental aspect of database system to create,
retrieve, update and delete a record. Ultimately, identification of database
record lays a solid foundation for CIA realization in information security. |
|||
|
Received 03 May 2024 Accepted 08 June 2024 Published 01 July 2024 Corresponding Author Musa
Midila Ahmed, ahmedmm4me@gmail.com DOI 10.29121/DigiSecForensics.v1.i1.2024.12 Funding: This research
received no specific grant from any funding agency in the public, commercial,
or not-for-profit sectors. Copyright: © 2024 The
Author(s). This work is licensed under a Creative Commons
Attribution 4.0 International License. With the
license CC-BY, authors retain the copyright, allowing anyone to download,
reuse, re-print, modify, distribute, and/or copy their contribution. The work
must be properly attributed to its author.
|
|||
|
Keywords: Identification System, Students’ Identification,
Information Security Key, Unique Identification, Human Resource
Identification, Material Resource Identification |
|||
1. INTRODUCTION
Security in this context refers to measures adopted by educational institutions to be protected against harm. It involves the protection of physical, network and electronic data from both intentional and/or unintentional harm. For an educational organizations, data is one of the most important asset. Therefore, protection of information from unauthorized access for use, disclose, discussion, modification or destruction is crucial. Information security is the act of protecting unauthorized access of organizational data. There are several categories of data educational institutions gather to use for planning and information purposes. These include data about learners, educators, administrators, workers, parents, visitors and resources. Educational data such as attendance, entry grades, assessment scores, graduation rates are vital ingredients for optimal evaluation of learners’ academic achievement. It is one of the most proven tool to inform and engage learners to create opportunity that leads to insights and improvement. Learners’ data empowers educational stakeholders; parents, administrators, policy makers, educators and learners with comprehensive information on the learning status of individuals and the institution. The goal of information security in modern organization are confidentiality, integrity and availability (CIA). The CIA is the core governing principle for good standing information security posture/ Availability in this context is the ability to make information and other information resources in education systems timely and reliably accessible where it is needed. According to Qadir & Quadri (2016), it is the assurance that information is accessible to authenticated and authorized users where needed. Identification is an evidence establishing that an individual or thing belongs to the group already known to the system. Identification in education systems is essentially a crucial aspect of an organization effectiveness. Authentication relates to ensure that data is available to identified legitimate users only. Authentication according to Menzel et al. (2007). is a process of establishing the legitimacy of communicating parties. Authorization policies defines what an individual identity or group may access, access controls are the method of enforcing the policies. Access control is a method of verifying the identity of users and guaranteeing that users have appropriate permission to access systems resources. Confidentiality is a security principle that ensures unauthorized people cannot get access to sensitive data. Data integrity breach renders transmitted data vulnerable to active attacks. Data integrity protection is important in maintenance of validity and accuracy of data and it is a protection from active attacks.
Information security technology is the defence of digital information and information technology assets from internal and external threats. Security is a critical aspect of educational organizations’ management of all sizes. Security technology systems should be modernized and updated to be in tandem with the continuously evolving cyber threats Pirc et al. (2016). The critical aspect of information security is the protection of data at rest and on motion from attackers. Therefore, education managers should implement effective information security program essential to protect the integrity and confidentiality of the organizations’ data as well as ensure information is available to authenticated and authorized persons.
2. Resources Identification in Education System
2.1. An Overview of resource Identification
The most important role of educational administrators is effective management of both human and material resources. Although many educational institutions have limited resources available for use to improve learning and enhance learners academic achievement. However, lack of resources is not the only cause of learners’ poor academic achievement. A range of human resources that are essential for the effectiveness of educational institutions include administrators, learners, instructors and supports staff. Availability and quality of materials resources is a basic necessity for delivery of quality education. Education organizations is responsible for protection of information systems by implementing effective security measures. The security measures should focus on the overall security of resources as well as increase efficiency and productivity in the education systems. The first stage of security design for education systems is the identification of both human and material resources available. A formal identity is any document or card issued to a human or material resources for identification purpose. The identity document issued establishes a connection between its holders with corresponding detail information stored in the database. The database for human resources may contain bearers’ full name, age, gender, date of birth, address, identification number, department, level, admission year, etc. Similarly, the database for material resources may contain detail information such as procurement year, department, identification number, etc. on assets and resources available.
2.2. Identification of Human Resources in Education Systems
Human resources is the people within an educational organization’s workforce that provide their skills and talents toward the overall success of the system. This refers to persons that trade their labour, knowledge, time and loyalty for compensation to enhance the organization. Identification and development of human resources is part of the process of enhancing the effectiveness of the organization. Basically, identification must be unique within a particular educational organization. This can be accomplished with the following common identification methods: Username, Unique identification Number, Smart Cards, Phone number and email Address. Username is the most often used by educational organization as a standard form of identification. Unique identification number is given to systems users for verification of their right of performing any action by the identity in education systems. A smartcard is a portable security token device with an embedded integrated chips to communicate with software in education systems. In addition to personal identification, Smartcard also provides authentication, data storage and application processing functions. Phone number and Email address are new forms of identification serving as a unique identifier of human resources in education systems. However, organization must use Phone number and Email address with other authentication controls for enhanced education systems security.
2.3. Identification of Material Resources in Education Systems
Material resources are things that can be used by people and considered to have value. Material resources refers to valuable items currently available in an educational organizations such as furniture, equipment, textbooks, technological materials, and any other useful objects. This include essential commodities that supports teaching and learning activities as well as proper administration of educational institutions. Efficient use of materials resources is an important factor for assuring adequate improvement of quality of any education systems. Although, this requires both the availability and quality of the materials. Therefore, educational institutions should ensure that learning materials are available and the quality is adequate for delivery of curriculum contents. It is critical that the available resources are maintained for provision of adequate and safe environment in education systems. The importance of integrating ICT in education systems is globally emphasized Abuhmaid et al. (2011) . Although, the use of ICT in education systems is limited due to the unavailability of these facilities in many educational institutions. Generally, ICT is recognized as a powerful tool for enhancing the quality of education systems. According to Usman (2016) , proper management of material resources would boast the moral of human resources as well as ensures the attainment of academic goals.
2.4. Unique Identification Systems
Unique identification serves as a useful and trusted essential basic proof of legal identity of every member of an organization or country. Identity refers to the combination of numeric, alphanumeric or inherent attributes that makes a person or material unique in a given context. The inherent attributes that makes a person unique include biographic data such as name, date of birth, address, etc. and biometric data such as fingerprint, facial recognition, etc. these identity attributes establishes a proof of person’s identity in a credentials format. These identity proofs is used in the process of authentication, authorization and access control by third parties. This is to ensure that they are really who they claim to be and to determines whether they are eligible for a specific right. The planning, design and implementation of identification systems for education systems can be in three (3) levels; organization level, national level and international level.
2.4.1. Organizational Identification Systems
Organizational identification refers to the ways organizations establish the identity of its human and material resource. Identification of human resources comprises of students and staff. Whereas that of materials resources comprises plants, machineries and equipment.
1) Identification
of Human Resources
Educational organization need to establish the identity of students admitted and staff employed at the point entry. Emphasis should be on uniquely assigning an identification credentials inform of numbers, cards, or identification certificate to all students admitted and personnel employed into the organization.
·
Students’ Identification
Students’ identification refers to assigning unique number for all learners in an educational organization. All learners in an educational institution should have identification (ID) card contains their name, unique identification number, and photograph. It is important for the student ID card to clearly have students’ picture, students’ personal details, identifying information and the institutions logo. The unique identification number on the ID card should be assign to students at the point of entry into the institution. It serves as the means of uniquely recognizing students throughout the study period and extends to post graduation of the students.
· Personnel Identification
According to Schreiber & Carley (2004), identification of personnel is crucial for any educational institution of learning. Moreover, as the size of educational institution increases, so also the significance of personnel identification
2) Identification
of Materials Resources
Materials resources is anything of useful value owned by the institution in the form of assets such as furniture, equipment, technological devices, curriculum materials, textbooks, etc. Adequate identification of these material resources help in their effective allocation and management. In addition, it could serve as a means of tracking their movement to curtail theft and unauthorized use of material resource.
2.4.2. National Identification Systems
The national identification systems is the means of tracking indigenes, permanent residence and visitors of a countries. It serves as a means of planning and administration of government services such as taxation, health cares, education, social services and other functions.
1) National
Identification Number (NIN)
The national identification number (NIN) is a unique number given to all individuals enrolled with the organization responsible for identity management in various countries. The assigned unique number serves as a means of authenticating individuals’ record in the national database.
2) National
Drivers’ Licenses
Drivers’ license is a card that proves an individual is officially and legally qualified to drive a specific category of vehicle within a country. A driving license is an official document issued to individuals who past the driving test conducted by government agency or accredited driving schools.
3) Voters’
Cards
A voter is a person qualified to vote in an election. A voter in a country is a person who has the legal right to vote in an election of the country. A voter identification card is an official and legal document empowering citizens to vote in elections in the country.
2.4.3. International Identification Systems
International identification systems is to provide identity credentials for the citizens beyond the scope of their country of origin World Bank Group (2016). The purpose of international identification is to provide people with proof of identity at the global level.
1) International
Passport
International passport (aka passport) is a document issued by government to its indigenes containing the person’s details information for identification purpose to verify holders’ citizenship.
2) International
Drivers Licenses
Similar to national drivers’ license, the international drivers’ license permits non-indigene drive a specific category of vehicle within a country. The license has detail information for establishing the identity of individuals in the foreign country. Consequently, this might be an acceptable identity proof of international students worldwide.
2.5. Biometric Identification Systems
Biometric is an effective ways of proving the identity of an individual by unique biological features. It enables the identification of specific person in a unique and verifiable manner. Biometric data serves two different purposes in education systems. First, the purpose of biometric identification is capture and keep the biometric data of people for proof of identity. It serves as the means of identification of genuine students of the institution. Second, it serves as authentication purpose of proving that the students are really who they claim to be. Biometric data can be broadly classified in physical and behavioural features. The physical attributes comprises of facial recognition, image of fingerprint, eye’s iris and retina, etc. whereas the behavioural features are characteristics’ such as record of voice, keystrokes dynamics, signatures recognition, etc.
1) Facial
Recognition
Facial recognition is a type of security technology that uses human face for identification and authentication of individuals. The key identification features in facial recognition include the size and structure of noses, eyes, ears, mouth as well as their positions on human faces. Hitherto, this technology is commonly used for critical security issues by law enforcement agencies to identify individual of interest such as criminals, fraudsters and impersonation during investigations. However, due to increase in need for security surveillance for the protection of schools, colleges and university campuses, this technology is now being implemented in the education sector Andrejevic & Selwyn (2020). The application of facial recognition in education sector ranges from attendance monitoring to campus security. Although, Yang et al. (2018) proposed facial recognition technology model to monitor students’ emotion in online educational services. Furthermore, it enables educational administrators know students and staff better crucial in detecting as well as preventing potential threats. Andrejevic & Selwyn (2020) are of the view that security critical services in education sector need to focus on application of facial recognition technologies.
2) Fingerprint
Technology
Fingerprint is an impression of fingertips and thumbs to establish the true identity of an individual using ink, sweat or any reagent that can be visible. This serves as an effective means of personal identification, since the patterns of ridges in every human being is unique. Fingerprint is the most popular method of biometric identification and authentication Prasad et al. (2018). Generally, the ridges of the fingerprint impression form patterns classified as; arches, loops and whorls on any surface touch such as glasses, tables or any surface as shown in Figure 1.
Figure 1
|
Figure 1 Classification of Fingerprint Patterns |
· Arch: This is an impression of the pattern whereby the ridges enter from one side and exit on the other side with a rise in the centre. Only about 5% of human population have this kind of fingerprint pattern.
· Whorl: This is a kind of fingerprint pattern with at least two deltas. About 35% of human population have this kind of fingerprint pattern.
· Loop: This is a pattern whereby one or more ridges enters in one side of the impression recurve either touch or pass over an imaginary line extension of the delta to the core and either end or tend to end at the entry ridges. This is the most common fingerprint patterns with about 60% of human population having this fingerprints
3) Voice
Recognition
Voice recognition is the ability of recording, analysing and interpreting human voice especially for identification of an individuals. The ability of computer systems to understand the person speaking by digital analysis of the recorded voice enables the identification of individuals in education sector. Khairi (2019) proposed voice identification and authentication solution to secure client and server mobile learning systems. Similar effort by Hu et al. (2020) used voice signal analysis to identify the person speaking. The benefit of using voice recognition according to the authors is that it increases the durability of the solution’s access code as well as the ability of confidential monitoring of user’s identity.
4) Eye
Iris & Retina Recognition
Human eye provide measurements that can be used for biometric identification. These measurements have been in use for identification and verification of people by governments’ security intelligence to track criminals. Although, eye-related metric technology is less popular compared to face recognition and fingerprint De Marsico et al. (2016). The two major categories of eye-related biometrics identification are the patterns of the iris and retina (see Figure 2) parts of the eye.
Figure 2
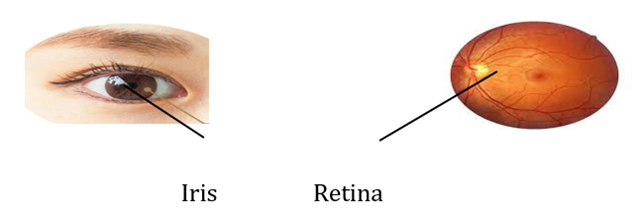
|
Figure 2 Iris and Retina of Human Being |
Iris recognition is a form of biometric technology that leveraged on the invisible unique patterns in the irises of people. Whereas, Retina recognition is a biometric system that uses the patterns of retina for identification of person. According to Sadikoglu & Uzelaltinbulat (2016), retina based identification is implemented in three stages; retina image acquisition, features extraction, and classification. First, retina image acquisition captures the unique patterns of blood vessels around the eyeball. Second, the digital image of the retina contains a diversity of unique features. This is converted into numerical values for classification and analysis. Finally, the classified features are analysed by neural network operations to recognize the unique patterns of each retina image.
5) Keystroke
Dynamics
Keystroke recognition is a behavioural biometrics individuals’ identification method by using person’s typing patterns. Attackers find various ways of stealing users’ identity credentials Agilandeeswari (2020). Consequently, keystroke dynamic is a novel and cost effective way of protecting data using only the keyboard as the hardware required. The et al. (2013) identified uniqueness, low cost, transparency, lifespan strength, no replicability, monitoring and authentication as the advantages of keystroke dynamics. However, the disadvantages of keystrokes dynamics according to the authors are less accuracy and permanency. Tsimperidis et al. (2018) used keystroke dynamics to identify the gender of system user. According to the authors, keystroke recognition could be a promising tool for alerting impersonation and identity suspects. The uniqueness of users’ stroke is leveraged by Usoof & Lindgren (2008) to establish the identity of individual English language writers. The authors discovered that stroke patterns can be used to distinguish between writers
6) Signature
Recognition
A signature is a mark written in a distinctive manner made by an individual on a document, cheque or letter as a form of identification in approval, acceptance or obligation. It authenticates and binds the writer with the provision contained in the document.
7) DNA
DNA is an abbreviation of Deoxyribonucleic acid, a
chemical molecule that contains genetic information in animals, plants and some
viruses. It is the base for information storage in all living things. DNA is
used in information security for identification of individuals. Just like
digital fingerprint, every person has a unique DNA that can be stored in
Educational Database System for identification of individuals.
3. Educational Database System
3.1. An Overview of Database System
Real world entities that can be individually identified are used to design a database. Database is a collection of related information or data organize to facilitate easy search and retrieval by a computer program. Information is stored, modified, deleted, and retrieved from the database in response to queries. Database model is a blueprint that is carefully designed to describe the structure of a database. An entity set is a collection of objects with the same types of attributes at any point in time. An entity is a uniquely identifiable and distinguishable real world object that can exist independently, Entities can either be strong entity that exist on its own or weak entity that only exist in association with other entity.
1) Strong
Entity
Strong entity is an entity type that has a key attribute, which helps in uniquely identifying each entity. A strong entity can be recognize by the existence of primary key in the set of its attributes. For instance, a student can be uniquely identified by registration number.
2) Weak
Entity
A weak entity cannot be uniquely identified by its own
attributes but relies on relationship with other entity. That is, more
attribute(s) is required to uniquely identify weak entity. The primary key of
weak entity is not sufficient to uniquely identify it as such requires
additional one or more attributes from parent entity as a foreign key. For
instance, room number of student is needed as part of dormitory information to
identify a student in the dormitory. In terms of DBMS, an entity is a table in database.
Entities are represented by a rectangle carrying the name of the entity set it
represent.
3.2. Attribute
An attributes are the properties or characteristics of an entity that uniquely identifies that entity in the real world. An attribute is represented by a column in relational database. Multivalued attribute has two or more value and is represented by double oval in relational database model. Multivalued attribute in a table is handled by first normal form of normalization that requires each table cell in the database should contain a single value. An example of multivalued attribute is address. A student can have more than one address, that is permanent address and temporary address. Attributes are classified into four (4) types.
1) Simple
Attribute
Simple attributes are atomic values, which cannot be divided further. For instance, a student's phone number is an atomic value of 10 digits.
2) Composite Attribute
Composite attributes are made of more than one simple attribute. In other word, a composite attribute is a combination of other attributes. For example, ‘Student name’ attribute that can divided into ‘First name’, ‘middle name’ and ‘Last Name’.
3) Derived
Attribute
Derived attributes are attributes whose value is dynamic and derived from another attribute. That is, they are the attributes whose values are derived from other attributes present in the database as such they do not directly appear in the database physically. For example, Person age can be dynamically derived from Date_of_Birth.
4) Key Attribute
Key attributes are the attributes that will uniquely identify the entity. Key attribute is usually represented with its text underlined in an oval. The three major types of keys are candidate key, primary key and foreign key.
· Candidate key: Candidate key is a key that identifies a record uniquely in a table but a table can have multiple candidate keys.
· Primary Key: A primary is a single column value used to identify a database record uniquely. In other word, primary key is a unique and non-null key, which identifies a record uniquely in table of a database.
· Foreign Key: A foreign key is a set of attributes in a table whose values matches values of the primary key of another table
3.3. Relationship
The basic concept behind relational database is the relationship between two database tables where one table uses a foreign key to reference the primary key of another table. The role of foreign key in a relational database table is to establish a relationship by linking a record of one database to data in another table, The three types of relationships that can exist between two entities in a relational database are one-to-one relationship, one-to-many or many-to-one relationship and many-to-many relationship.
1) One-to-One Relationship
One-to-one relationship is established between two tables when each record of one table is related to only one record of another table of a relational database. For example, if there are two entities ‘Professor’ (Id, Name, Age, Address) and ‘Office’ (Office_Id, Office_Block). So that each professor can have only one office and each office should belongs to only one.
2) One-to-Many Relationship
This is a kind of relationship whereby each record of one table is associated to one or more record(s) of another table in relational database. For example, many students can study in a single department but a student cannot study in many department at the same time.
3) Many-to-many Relationship
Many-to-Many relationship is established between two entities when more than one instances of an entity is associated with more than one instances of another entity in a relational database. It is a relationship whereby each record of the first table is related to more than one record of the second table and conversely, For example, a student can offer many courses and a courses can be assigned to many students.
4. Conclusion
Identification of entities is a fundamental aspect of database system. Identification enables the capability to find, retrieve, report, change, or delete specific data information stored in databases without ambiguity. Data identification link separate records of information on the same entity. Unique identifiers also known as keys in a database is used to distinguish one information from the other, in information security perspective, protection of electronic records and other digitally stored data can be achieved effectively by unique identification of systems’ users. Identification of database records lays solid foundation for authentication, confidentiality and data integrity goals of information security.
CONFLICT OF INTERESTS
None.
ACKNOWLEDGMENTS
The author acknowledged the support and encouragement of the council and management of Modibbo Adama University Yola, Nigeria.
REFERENCES
Abuhmaid, A. (2011). ICT Training Courses for Teacher Professional Development in Jordan. Turkish Online Journal of Educational Technology-TOJET, 10(4), 195-210.
Agilandeeswari, L., Ragul, V., Nihal, S. S. M., & Khan, M. R. (2020, December). A Comprehensive Analysis of Keystroke Recognition System. In International Conference on Intelligent Systems Design and Applications Springer, Cham. https://doi.org/10.1007/978-3-030-71187-0_99.
Andrejevic, M., & Selwyn, N. (2020). Facial Recognition Technology in Schools: Critical Questions and Concerns Learning. Media and Technology, 45(2), 115-128. https://doi.org/10.1080/17439884.2020.1686014
De Marsico, M., Frucci, M., & Riccio, D. (2016). Eye Biometrics: Advances and New Research Lines. Elsevier Pattern Recognition Letters. http://dx.doi.org/10.1016/j.patrec.2016.05.003.
Hu, Z., Tereikovskyi, I., Korystin, O., Mihaylenko, V., & Tereikovska, L. (2020, January). Two-Layer Perceptron for Voice Recognition of Speaker's Identity. In International Conference on Computer Science, Engineering and Education Applications Springer, Cham, 508-517. https://doi.org/10.1007/978-3-030-55506-1_46.
Khairi, T. W. A. (2019). Secure Mobile Learning System Using Voice Authentication. J. Eng. Appl. Sci, 14(22), 8180-8186. https://doi.org/10.36478/jeasci.2019.8180.8186.
Menzel, M., Thomas, I., Wolter, C., & Meinel, C. (2007, November). SOA Security-Secure Cross-Organizational Service Composition. In Proceedings of the Stuttgarter Softwaretechnik Forum, 41-53.
Pirc, J., DeSanto, D., Davison, I., & Gragido, W. (2016). Threat Forecasting: Leveraging Big Data for Predictive Analysis. Syngress. https://doi.org/10.1016/B978-0-12-800006-9.00002-1.
Prasad, P. S., Devi, B. S., Reddy, M. J., & Gunjan, V. K. (2018, January). A Survey of Fingerprint Recognition Systems and Their Applications. In International Conference on Communications and Cyber Physical Engineering, Springer, Singapore, 513-520. https://doi.org/10.1007/978-981-13-0212-1_53.
Qadir, S., & Quadri, S. M. K. (2016). Information Availability: An Insight into the Most Important Attribute of Information Security. Journal of Information Security, 7(3), 185-194. https://doi.org/10.4236/jis.2016.73014.
Sadikoglu, F., & Uzelaltinbulat, S. (2016). Biometric Retina Identification Based on Neural Network. Procedia Computer Science, 102(1), 26-33. https://doi.org/10.1016/j.procs.2016.09.365.
Schreiber, C., & Carley, K. M. (2004). Key Personnel: Identification and Assessment of Turnover Risk. Proceedings of NAACSOS.
Teh, P. S., Teoh, A. B. J., & Yue, S. (2013). A Survey of Keystroke Dynamics Biometrics. The Scientific World Journal. https://doi.org/10.1155/2013/408280.
Tsimperidis, I., Arampatzis, A., & Karakos, A. (2018). Keystroke Dynamics Features for Gender Recognition. Digital Investigation, 24, 4-10. https://doi.org/10.1016/j.diin.2018.01.018.
Usman, Y. D. (2016). Educational Resources: An Integral Component for Effective School Administration in Nigeria. Online Submission, 6(13), 27-37.
Usoof, H., & Lindgren, E. (2008). Who is Who and Doing What in Distance Education?: Authentication and Keystroke Dynamics. Tidskrift för Lärarutbildning Och Forskning, (3-4), 175-187.
World Bank Group (2016). Identification for Development: Kenya. World Bank.
Yang, D., Alsadoon, A., Prasad, P. C., Singh, A. K., & Elchouemi, A. (2018). An Emotion Recognition Model Based On Facial Recognition in Virtual Learning Environment. Procedia Computer Science, 125, 2-10. https://doi.org/10.1016/j.procs.2017.12.003.
|
|
 This work is licensed under a: Creative Commons Attribution 4.0 International License
This work is licensed under a: Creative Commons Attribution 4.0 International License
© DigiSecForensics 2024. All Rights Reserved.